Windows Share Enumeration checks for Windows shares that are readable by Everyone and returns the number of files for each share on each host. This feature is supported for both vulnerability scans and compliance scans.
The Dissolvable Agent (Agent) is installed on Windows devices to collect host data in order to perform certain scans. During the scan process the Agent is installed as needed. Once the scan is complete, the Agent will remove itself completely. Windows Share Enumeration requires that a Manager accept the Agent for the subscription. A Manager can accept the Agent (if not already accepted) by going to Setup > Dissolvable Agent and clicking the Accept button.
1. Select Option Profiles from the left menu. Then create or edit an option profile.
2. In the Option Profile window click the Advanced button.
3. Navigate to the Share Enumeration section and select Windows Share Enumeration. (If this option is disabled, then the Dissolvable Agent has not been accepted for the subscription. See Step 1 above.)
Note: Windows authentication is required for Windows Share Enumeration. If Windows authentication is not already selected for the option profile, the service will automatically select it when you select Windows Share Enumeration. A Windows authentication record is required.
4. Navigate to the Vulnerability Detection section. The Windows Share Enumeration testing requires that vulnerability QID 90635 is included. If Complete is selected this QID will be tested. If Custom is selected, be sure that QID 90635 is included in the associated search lists. If Excluded QIDs is selected be sure that QID 90635 is not included in the associated search lists.
5. Click the Save button to save the option profile.
1. Select Option Profiles from the left menu. Then create or edit a compliance profile.
2. Navigate to the Control Types section and select Windows Share Enumeration. (If this option is disabled, then the Dissolvable Agent has not been accepted for the subscription. See Step 1 above.)
3. Click the Save button to save the compliance profile.
Windows Share Enumeration requires administrator / root level authentication. Create Windows authentication records with administrator / root privileges. See Creating Windows Records.
Vulnerability Scan. Launch or schedule a vulnerability scan on the hosts you want to scan for Windows Share Enumeration. Apply an option profile with the option Windows Share Enumeration selected and with the vulnerability QID 90635. If your option profile does not include all vulnerability checks, then be sure QID 90635 is included.
Compliance Scan. Launch or schedule a compliance scan on the hosts you want to scan for Windows Share Enumeration. Apply a compliance profile with the option Windows Share Enumeration selected.
For additional information see Launching Scans and Scheduling Scans.
The Windows Share Enumeration findings from your scan appear in vulnerability scan results and in template based reports. Specifically, this information appears in Detailed Results in the Results section.
Generate a vulnerability scan report to view scan findings. If Report Share is enabled for your account see Running Reports from Report History List. If Report Share is not enabled see Running Reports from Report Templates List.
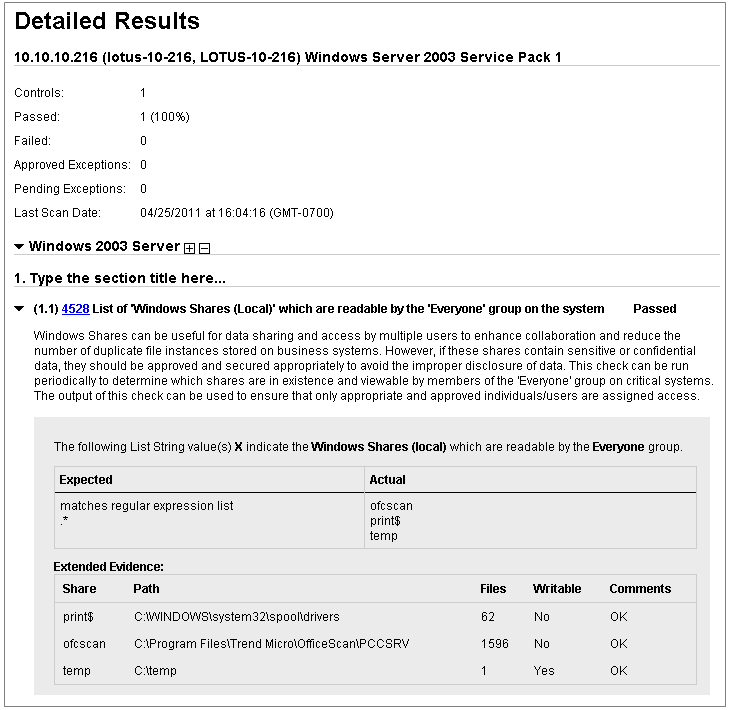
In the sample report below, the Detailed Results for host IP 10.10.10.216 shows three shares that are viewable by Everyone within the RESULTS section.
Columns in RESULTS section: The Share column shows the share name. The Path column shows the path to the share. The Files column shows the number of files found in each share. The Writable column indicates whether all the files in each share are writable by Everyone (Yes/No). In the Comments column "OK" indicates that the scanning engine finished counting the files in the share. "Limited" indicates that the scanning engine either a) reached its time limit before finishing the file count, or b) reached its maximum number of files to count. If Comments is "Limited", this implies the number of files in Files may be less than the actual value.

Generate a compliance report to compare the data gathered on your hosts during your compliance scan to the expected values defined in your compliance policy. See Running Policy Compliance Reports.
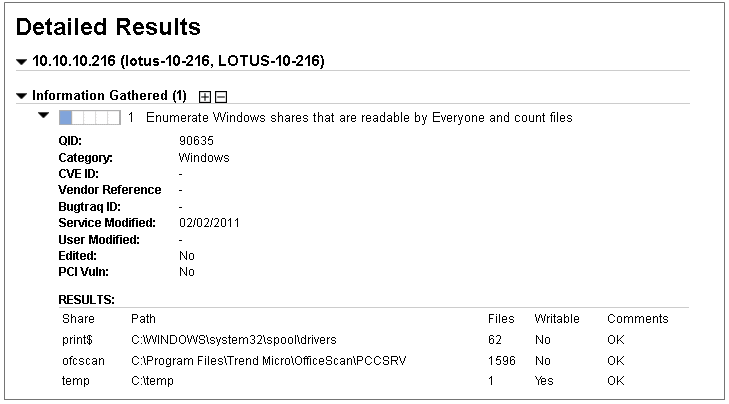
In the sample below, the Detailed Results for host IP 10.10.10.216 shows three shares that are viewable by Everyone within the Extended Evidence section.
Columns in Extended Evidence section: The Share column shows the share name. The Path column shows the path to the share. The Files column shows the number of files found in each share. The Writable column indicates whether all the files in each share are writable by Everyone (Yes/No). In the Comments column "OK" indicates that the scanning engine finished counting the files in the share. "Limited" indicates that the scanning engine either a) reached its time limit before finishing the file count, or b) reached its maximum number of files to count. If Comments is "Limited", this implies the number of files in Files may be less than the actual value.