To get to this page: Go to Setup > Business Risk.
Business risk is determined by two factors: security risk and business impact. Security risk is calculated by the reporting engine when you generate a scan report. Business impact is user-defined and assigned to asset groups. When you generate scan reports based on current host/vulnerability data, the reporting engine calculates security risk for asset groups/hosts in the report and uses the business risk table to perform a lookup for the business risk value to display in your report.
See the following for more information:
Initial business risk settings are provided. It's recommended however that you perform business impact analysis on assets in your organization and apply those findings to business risk values and titles.
Managers have the option to customize any of the following:
• Business risk values. Edit business risk values to increase or decrease the weight or importance applied to any security risk/business impact level.
• Business impact titles. Edit business impact titles to match the terminology used in your organization. For example, if your organization uses the term "Code Red" to identify the most critical issues, then you can change "Critical" to "Code Red"
• Method used to calculate security risk. The security risk configuration for your subscription determines how security risk is calculated at the "Detailed Results" level of scan reports (Auto). Security risk may be equal to the highest severity level detected or the average severity level detected for your sorting criteria. The security risk configuration may be defined to include or not include hosts with no vulnerabilities. You set the security risk configuration on the Security Risk Setup page (Setup > Security Risk).
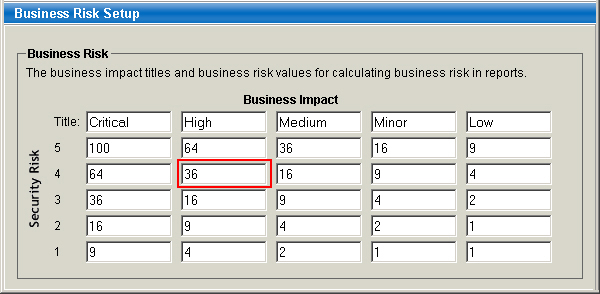
To calculate business risk for a particular asset group, the reporting engine uses the business risk lookup table to find the business impact level assigned to the group and the security risk calculated for the group. For example, if Asset Group A is assigned a business impact level of High and the security risk calculated for this group is 4, then the business risk is 36, as highlighted in the table below.

When security risk falls between two values in the business risk lookup table, a linear interpolation between the two values is calculated. The following examples use data from the sample table above.
If security risk is 3.4 and business impact is High, then business risk is calculated using the following method:
Business risk for security risk 4 = 36
Business risk for security risk 3 = 16
Business risk for security risk 3.4 = 16 + [0.4 * (36-16)] = 24
If security risk is 4.7 and business impact is Critical, then business risk is calculated using the following method:
Business risk for security risk 5 = 100
Business risk for security risk 4 = 64
Business risk for security risk 4.7 = 64 + [0.7 * (100-64)] = 89.2
Note that the decimal is dropped in the report so business risk will appear as 89.
Business impact levels are assigned to asset groups and thus to the hosts included in those groups. Initially, impact level titles are Low, Minor, Medium, High and Critical. Managers can change these titles to match the terminology used in your organization. For example, if your organization uses the term "Code Red" to identify the most critical issues, then you can change "Critical" to "Code Red". The new title will appear in business risk reports and may be assigned to groups.
When determining which impact level to assign an asset group, think about how critical the group of hosts is to your organization. The higher the impact level, the higher the potential for business loss if compromised. For example, you may apply a higher impact level to an asset group of Linux servers running mission critical applications than to an asset group of desktop systems. If an impact level is not assigned to an asset group, then a level of High (or its equivalent) is automatically assigned.