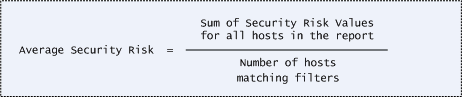
The Summary of Vulnerabilities section of your scan report shows the average security risk value for all hosts in the report (hosts matching filters). Security risk is first calculated for each host in the report. Then the average of the security risk values for all hosts is calculated and displayed in the summary. Important: The filters set in the scan report template will affect the number of hosts and the types of vulnerabilities that appear in your report.
This description of security risk applies to scan reports generated from scan report templates. See Security Risk in Scan Results for a description that applies to the Scan Results report.
The Summary of Vulnerabilities section of the scan report (Auto or Manual) shows the average security risk for all hosts in the report.
These factors are used when calculating the average security risk:
• security risk for each host (the highest severity level detected or the average severity level detected, see below)
• number of hosts matching filters (hosts in the report matching the filters set in the scan report template)
Note that the average security risk for the report displays the average for all hosts in the report, and is not affected by the sorting method applied to the Detailed Results section (see Security Risk in Detailed Results below).
The following formula is used for calculating the average security risk.

This section describes how security risk is calculated for each host in the report. The security risk calculation includes vulnerabilities and potential vulnerabilities. This calculation does not include information gathered.
In a Manual scan report, security risk is equal to the highest severity level detected across all vulnerabilities and potential vulnerabilities on the host. For example, if the highest severity level detected on the host is severity level 4 (whether confirmed or potential), then the security risk for the host is 4.
In an Auto scan report, the security risk calculation method is either 1) the average severity level detected, or 2) the highest severity level detected. The calculation method used depends on the security risk configuration enabled for the subscription. The security risk configuration may be defined to include or not include hosts with no vulnerabilities. Managers define configuration settings on the Security Risk Setup page (Setup > Security Risk). See Security Risk for more information.
See examples below of the security risk value as it appears in the Detailed Results section of an Auto scan report. Note that to see the security risk value in the Detailed Results section of the report, you must select the "Text Summary" option under Detailed Results in the scan report template. In the examples below, detailed results are sorted by host, the "Text Summary" option is selected in the scan report template, and active vulnerabilities and potential vulnerabilities are included in the report.
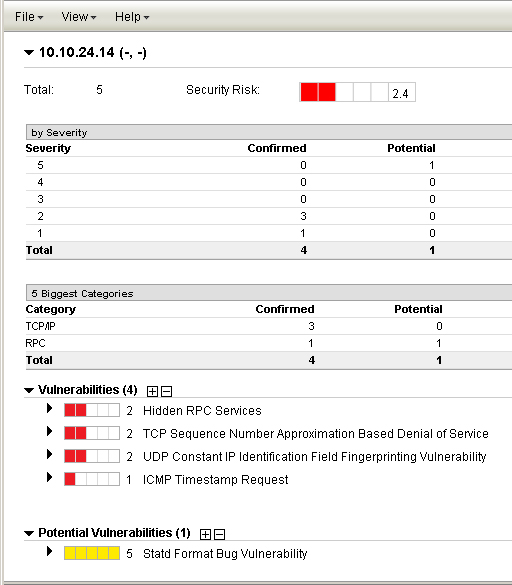
Example 1: Security Risk is set to "Average severity level detected":
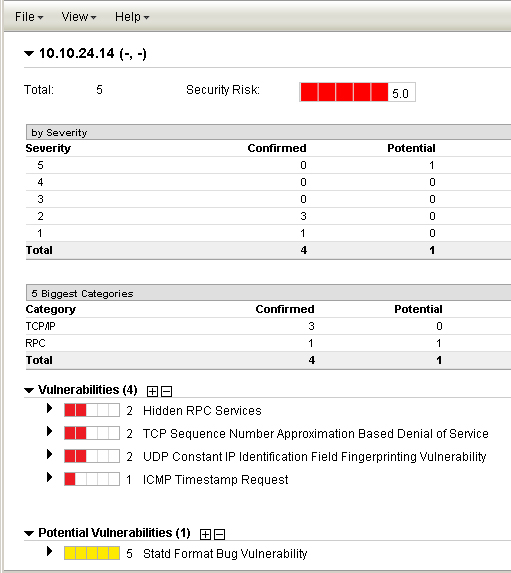
Example 2: Security Risk is set to "Highest severity level detected":
Note: To view security risk in the Detailed Results section of your Auto scan reports, you must edit the scan report template and select the option "Text Summary" under Detailed Results on the Display tab. Note that this option is not available in Manual scan reports.
The security risk value displayed in the Detailed Results section of the scan report is the security risk for all hosts that match the sorting method. The Detailed Results section of your report may be sorted by host (the default), vulnerability, operating system, asset group, service or port. You set the sorting method in the scan report template.
For example, if you sort detailed results by host, then the security risk displayed for each host is based on the vulnerabilities and potential vulnerabilities detected on the host. If you sort detailed results by some other method like operating system, then the security risk displayed for each operating system is based on the vulnerabilities and potential vulnerabilities detected on the hosts with that operating system. If you sort detailed results by asset group, then the security risk displayed for each asset group is based on the vulnerabilities and potential vulnerabilities on the hosts in that asset group, and so on. The same methodology applies to the other sorting methods.
Note that the average security risk for the report (in the Summary of Vulnerabilities section) represents the average risk for all hosts in the report, and is not affected by the sorting method used in the Detailed Results section.