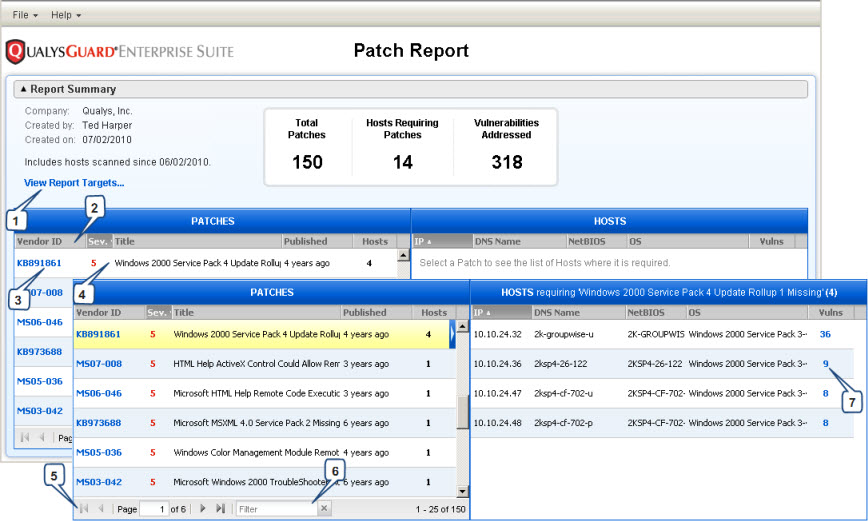
This online patch report summary shows: 150 total patches need to be applied to fix the vulnerabilities on the target hosts, 14 hosts require patches to be applied in order to fix the vulnerabilities, and 318 vulnerabilities in the user's account are addressed in the report.

(1) To view the target asset groups and/or IPs: Click "View Report Targets".
(2) To sort the patch list by patch attribute: Click a patch attribute (column title) in the PATCHES list. The arrow next to the column title indicates the sort order: ascending (Up arrow) or descending (Down arrow). Click the column title again to toggle the sort order.
(3) To read the vendor's security bulletin related to a patch: Click the vendor ID link for a patch in the PATCHES list.
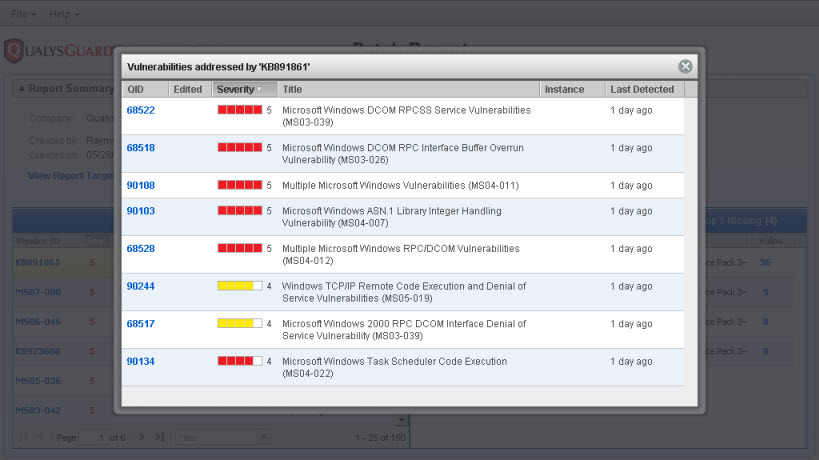
(4) To view the hosts that require a specific patch: Move your mouse pointer over a patch in the PATCHES list and click the patch row. The hosts requiring the patch appear in the HOSTS list (on the right). In the HOSTS header you'll see the number of hosts that require the selected patch. In this case, there are 4 hosts that require patch KB891861.
(5) To page through the PATCHES list: Use the arrow keys (under the list area) to page forward and backward through the list. Enter a number in the field provided to jump to a certain page number.
(6) To apply a filter to the PATCHES list: Enter a string in the Filter field (under the hosts list). The PATCHES list will be updated to display only patches with attributes matching the string you enter. For example, if you enter "Unix" the report will display only patches including that string.
(7) To view the vulnerabilities that will be fixed after applying a patch on a host: Refer to the Vulns column for a patch in the HOSTS list to view the number of vulnerabilities that will be fixed. If "QIDs that will be fixed by each patch” is selected in the patch template used to generate the report, click the number of vulnerabilities link to view a list of vulnerabilities the patch will fix. You'll notice instance data for the detection if applicable, and the age of the detection. If you click the QID, you will see the vulnerability information from the KnowledgeBase.