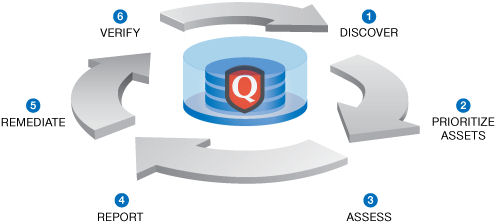
Vulnerability Management automates the lifecycle of network auditing and vulnerability management across the enterprise. This solution allows security managers to audit, enforce and document network security in accordance with internal policies and external regulations.
Vulnerability Management lifecycle:

1. Discover all assets across the network by running maps, and identify host details including operating system and open services.
2. Prioritize Assets to manage your network by categorizing assets into groups and optionally into business units. You may prioritize each asset group based on business criticality.
3. Assess security vulnerabilities on a regular basis and determine a baseline risk profile.
4. Report the level of business risk associated with your assets and trend overall security posture over time. Report Share is an optional feature that provides enhanced reporting capabilities for customers with large amounts of report data, and promotes collaboration and sharing of reports.
5. Remediate and fix vulnerabilities by business risk using recommended solutions, such as patches and workarounds. These solutions have been tested and verified by our own security experts. You have the option to manage vulnerabilities through remediation tickets.
6. Verify the elimination of threats and confirm security posture through follow-up scans.